Internet monitoring, corporate cyber snooping, internet filtering, e-mail scanners, key loggers, computer monitoring, pc surveillance, employee monitoring software, network monitoring, spy software… What ever you call it, like it or hate it, surveillance applications are being introduced to workplaces like never before. Even though questions concerning privacy remains, employers and IT managers know they must move on. Actions are taken. And surveillance software is deployed.
Computer/Internet surveillance software is an IT system deployed in a network to monitor and control end users’ computer and Internet activities.
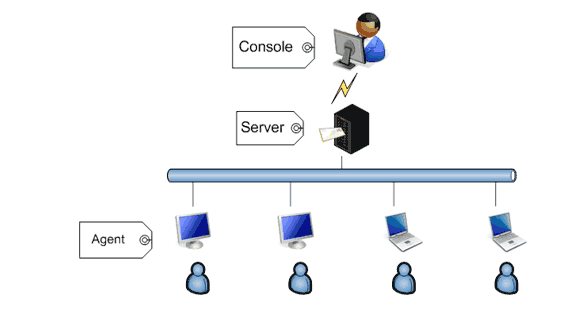
Such surveillance system is typically consisted of agent applications, installed in computers needed to be monitored and controlled, and control applications, used by IT managers or supervisors. Comprehensive systems may require a data base and a server. Take SurveilStar for instance:
Before judging whether it’s necessary to use such kind of employee monitoring software to monitor and control their computer and Internet activities, take a look at these facts:
In a computer-and-Internet-dominated workplace, only the Big Brother camera is not enough to secure your business.
When they seem to be working in front of computers, some slackers might be abusing computer and Internet in many ways: playing online games, sneaking a look at naked people on the Internet, circulating jokes or snide remarks about colleagues via emails, seeking jobs, shopping on eBay or Amazon.com, chatting with buddies via Instant Messengers... All these take place during the nine-to-five working day.
Even worse, some bad guys would steal business secrets or sabotage corporate information, especially when they have to leave the company. Companies will have to look closely at how they allow workers use corporate computers, emails and Internet resources.
Basically, there are four principal groups who use tracking software:
From the day we program this software, we have great anticipation on it, just as you do now. So we name it SurveilStar, hoping it can really help you out and become one of the shinning stars among the surveillance software industry.
The use of SurveilStar will not bother employers at all. SurveilStar runs silently in backstage, no visible interface or entry in the end user computer. And SurveilStar will not cause inconveniences to normal use of computer and Internet. Thus it’s a happy solution for both employees and employers. Download and review SurveilStar on software download web sites
What is the criterion of perfect computer/Internet surveillance? Or, what is the best practice of such kind of surveillance?
The answer is: the boss is happy with it, and the workers are happy with it, too. How to make this happen? Here are some general suggestions for your reference.
Even though SurveilStar can virtually monitor and control every computer/Internet activity, it might not necessary to restrict everything in practice. Only monitor and control what is necessary.
Outline a surveillance strategy, and then follow this strategy to create explicit policies.
Employer and IT manager should take into consideration:
Of course you can deploy the surveillance system across the whole network, on every chosen computer, while they are off work. And the stealth mode of SurveilStar Agent makes it impossible for employers to sense its existence.
Nonetheless, if you can openly declare the use of the surveillance system, and make your employees understand that the purpose is not snooping, but reducing potential legal troubles due to Internet/email abuse and increasing productivity. The company performs better, everybody benefits.
Well communication also includes the promise of protecting privacies.
An extreme case of computer/Internet monitoring is to forbid everything at first, and then allow only what is necessary and work-related.
Think twice. You can make the office hemisphere more active and positive even everybody knows their computers are being monitored.
How to make it? Do not tighten up too much. Let the mouse dance some time during the day, usually at rest time.
For instance, for some time during the day, you can allow them to watch YouTube videos, listen to iTunes music, browser Yahoo!, blog on MySpace…anything that does not harm to the company, but will refresh workers’ energy and creativity.
Employers want to be sure their employees are doing a good job, but employees don't want their every sneeze or trip to the water cooler logged. That's the essential conflict of workplace monitoring.
Computer/Internet surveillance in workplace is a business –is-business thing. Employers should not take advantage of the surveillance to snoop employees’ privacies. At the meantime, employees should not take personal things to workplace in office time.
From a legal perspective, a balance between corporate rights and employer’s privacy is even more important.
Data theft and sabotage is a growing problem primarily perpetrated by office workers. Since employees often feel they have some right to the corporate information and are inclined to copy and/or delete part of it when they leave the company, or misuse it while they are still in employment.
The most pilfered items include e-mail address books, customer databases as well as proposals and presentations.
Many of those stealing from companies send the purloined data to their personal e-mail account held at home or on the web. A small number, 21%, burned the information onto CDs. Other means, such as laptop computers, flash drives, iPod and even digital cameras, are also used.
There can't be many office-workers who don't sometimes play games on their computers, or sneak a look at naked people on the Internet. Email is often used to circulate jokes or snide remarks about colleagues. Most people probably regard it as harmless fun.
But employers can't see it that way. They may be legally liable for downloaded obscenity or defamatory emails. And they don't like their staff wasting time. And white collar employers are increasingly alarmed at just how much time is wasted surfing the internet each day.
A survey has found that many workers at small and medium businesses are wasting time with e-mail messages and websites that have nothing to do with their jobs. It found that 30% of the companies questioned were losing more a day's work per week to this time wasting. Any company that comprehensively tackled the time wasting could see profits jump by 15%.
Many large firms have suffered public embarrassment, legal bills, compensation claims and clear-up costs when employees seek out inappropriate material online, send e-mail to people they shouldn't, accidentally circulate confidential information outside a business or spread a computer virus.
A survey revealed that 44% of businesses have suffered an e-mail breach and that the average cost of clearing up after such a breach was £33,000. That is money few small and medium enterprises can afford.
Surveillance software has been a source of controversy ever since its commence. While companies claim that the programs are used to protect business and enforce computer policies at workplaces, there has been criticism that this invades users' privacy.
Other critics say that these software programs, especially if they have keylogging capabilities, can be used for malicious or criminal purposes, such as identity theft and unauthorized access to other systems.
Above all controversies, computer/Internet surveillance, especially email surveillance, is endorsed and even required by legislatures.
Regardless of any opinion or argument, one thins is crystal-clear: computers and network resource are corporate assets, and employers pay every single working hour, so they need to make sure that these assets and working hours are productive.
Supervisors can not sit behind employees and watch them all day long. The only solution is adopting surveillance system. At the meantime, employees might have to watch their online behavior as well as computer operations.
The introducing of computer/Internet surveillance software is not for the sake of snooping people’s privacy, but for the sake of protecting business and improving productivity. The explicit existence of monitoring system is also a remainder telling employees what their obligations are.