Document usage tracking is important to a company, it helps IT manager to know all the document usage logs. Once any confidential documents are leaked out, IT manager can track the leakage source easily using SurveilStar's document logs.
SurveilStar has powerful document usage recording functions and can record all operations on documents including Microsoft Office Documents like Word (*.doc, *.docx), Excel (*.xls, *.xlsx) and Powerpoint (*.ppt, *.pptx), Images like JPG, BMP, PNG, GIF, etc, Text(*.txt), PDF(*.pdf), HTML files(*.htm, *.html, *.php, etc.), Ebooks(*.epub, *.chm) and any other kinds of document files. Meanwhile, SurveilStar will record all kinds of operation types including Create, Copy, Move and more.
Select a computer or a group at first, then specify your search conditions including time and range, operation type, drive, source file, path, size, application, etc.
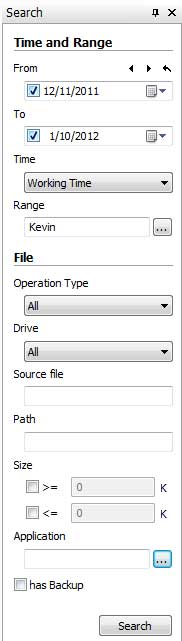
Operation Type: SurveilStar's document logs function supports all kinds of operation types including Create, Copy, Move, Rename, Restore, Delete, Access, Modify, Upload, Download and Burn.
Drive: The type of the drive where the operated documents locate in. Supported drive types include Fixed Drive, Floppy, BD-ROM/DVD-ROM/CD-ROM, Removable Drive and Network Drive.
Source File: File name of operated document. File extension could be included as well.
Path: The datailed location of the operated document. When Operation Type is Copy, Move or Rename, SurveilStar will record original path and target path.
Size: Specify file size to search the operated documents.
Application: Search operated documents with specific application which is used to open the documents. Click ... button to open the setting dialog. The settings are same as what is explained in previous chapter of Application Logs.
has backup: When using document policy or IM file policy, we can enable backing up the operated documents or sent/received files via instant messgeners. Once this option is checked, only files which have backup copy will be displayed. And you can save the backup documents and check the details of the documents. Document policy and IM file policy will be discussed in later chapters. The following pictures indicate that the deleted, modified and uploaded documents have been backed up.
![]()
![]()
![]()
After specifying your search conditions, click Search button to view the result. Below is a search result example of document logs.
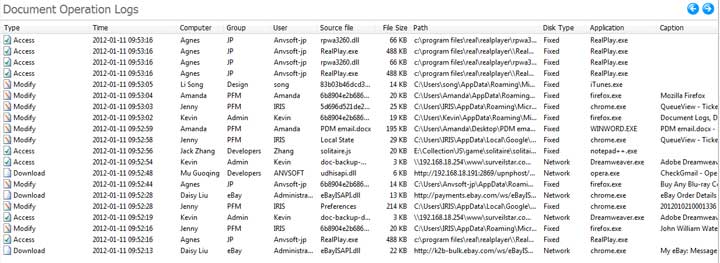
Right-click on a document log and click Property to view detailed information of this document operation. Time, Computer, User, Operation Type, File Name, File Type, Size, Drive, Path, Application and Window Title. If the file has been backed up, you will find a Copy button and you can click it to save the attachment.
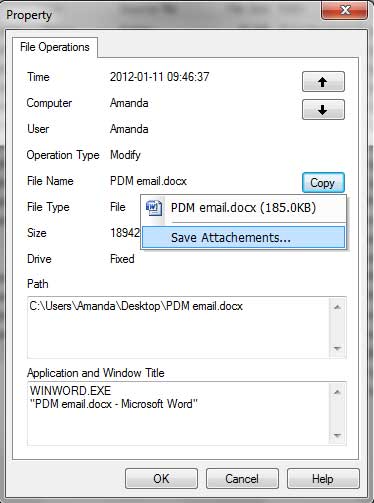
When operation type is Copy, Move or Rename, both original path and target path will be displayed. Below is an example.
| Web Logs | Back to Index | Shared File Logs |