Network policy can effectively control the communication between client machines and other illegal computers to block malicious port and prevent virus attacks, achieving to protect the internal network security.
As constantly watching over network state of monitored computers, administrators can efficiently control the network security of client machines by preventing them from malicious access and attacks.
In SurveilStar Console, click menu Advanced > Network, click Add button to create a network policy. Then you will see Property panel on the right as the picture below. In the following example, you can see that system would ignore but alert when client machine communicates with other computers.
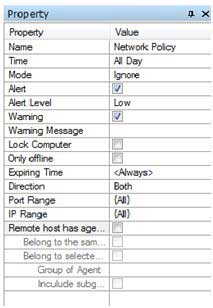
Name: Give your network policy a name like Network Policy.
Time: Set effective time for your network policy.
Mode: Select policy execution mode. Allow, Block and Ignore modes are available.
Alert: Enable or disable alert. Once IT manager or supervisor logs on SurveilStar Console, he will see the alert and know who has tried to break the network policy.
Alert Level: Choose alert level if Alert is enabled. Low, Important and Critical are available.
Warning: Enable or disable Warning.
Warning Message: Set warning message if warning is enabled. Anyone who breaks the network policy will see this warning message on monitor's screen center.
Lock Computer: Once this option is checked, the computer of the users who tried to break the network policy will be locked. IT manager can unlock the computer using menu "Control > Unlock" in SurveilStar Console.
Only offline: Check this option if you want the policy to be effective only when the computers are offline.
Expiring Time: Set expiring time for this network policy. Or leave it to Always to make it always effective.
Direction: Physical communication direction, including bi-directional, outbound and inbound. Client machine actively connects to other computers is defined as outbound, and on the contrary as inbound.
Port Range: Set port range used in the communication, which is all by default, including TCP port from 0 to 65535 and UDP port from 0 to 65535 and ICMP. You can not only manually add the port or port range individual, but also can specify category from the port classification by {…}.
Enter a specified port should proceeded by "TCP:" or "UDP:" to distinguish TCP port or UDP port, and if not, it will consider to be a TCP port.
IP Range: Set IP address range of the communication computers, which is all by default. You can not only manually add one by one, but also can specify category from the network address classification by {…}.
Remote host has agent installed: To judge whether the remote host is agent or not. It would not judge if not checked.
Only after checking this option can be able to set the following attributes:
- - - Belong to the group: Control communication between client machines belong to the same group. Which means the current group, and not only does not include subgroups but also not contain the upper layer of the group.
- - - Belong to selected group(s): Control communication between client machines belong to selected group. Only after checking this can you specify the group of agent below.
- - - Group of Agent: Specify the group of agent. Only after setting the group can you choose whether to include subgroup or not below.
- - - Include subgroup: Choose whether to include subgroup in the selected group(s).
There are two examples which can help you better understand Network Policy.
First One: The requirement is that when employee is on work, ftp download is forbidden. To achieve this, you can create a network policy like below.
1. Create a network policy.
2. Select the Block mode, set IP Range as all, set Port Range as TCP: 21.
Afterwards, ftp download will not be allowed to employees during working time.
Second One: The requirement is that computers of some departments across the enterprise should be very important and sector outside is not allowed to connect. To achieve this, a set of strategies is a good choice. For example:
1. Create a network policy and set network block to all IP range.
2. Create another network policy, and add specified agents belong to the same group to Allow mode.
Afterwards, only computers within the same department can communicate with each other.
Before setting policies such type, computers of the same department should set to be in the same group. And if there are computers do not have agent installed in the department, set a policy and add the IP range to Allow mode.
Please note that: Network Policy is available only for the computer, but invalid for the user.
| Bandwidth Policy (Advanced) | Back to Index | Email Policy (Advanced) |