SurveilStar -- Monitor Employee's Network Activities
Whatever you can monitor, you can control it. You can control certain computer’s access to websites, filter outgoing files via IM, block email attachment, disable removable device drive, cancel unauthorized file sharing, prevent changing system configurations, etc.
Features
- Take Screen Snapshots
- Email Monitoring
- Instant Message Monitoring
- Website Visit Monitoring
- Application Monitoring
- Document Monitoring
- Printing Monitoring
- Network Monitoring
- Computer Maintenance
- Data & User Management
Resources
- Complete Online Guides
- Video Tutorials
- SurveilStar Testimonials
- Deploying SurveilStar
- SurveilStar Home Edition
- Free Activity Monitor
- Free Email Recording
- SurveilStar Press Release
- Version Comparison
- Feature Module Comparison
- 日本語
- français
Topics
Insiders a majoy security threat
Last few years,Craig Goldberg's start-up came face to face with a more sinister threat that would take it to the brink of disaster: cybercrime.
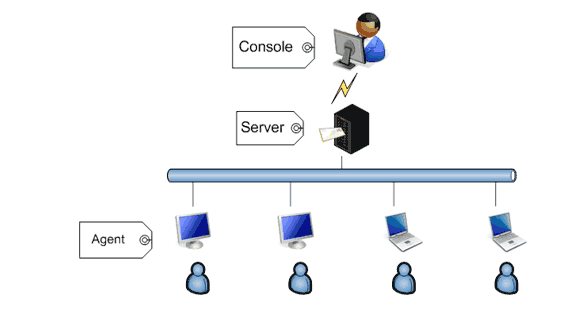
SurveilStar is the trustworthy PC/Internet monitoring software that helps to secure your business and improve productivity and efficiency. SurveilStar is feature-rich, easy and intuitive.
With the real-time screen snapshots and dynamic control strategies, you are in control of everything: stopping sabotage and data theft, reducing workplace slackers...
Cybercrime cause big cost
Many legal and sucurity experts encourage employers to monitor Interner activity as a proactive measure, to protect themselves against potential litigation from their employees and the daily increase cybercrime.Such harassment and discrimination lawsuits have proven to be very costly for employers who failed to diligently monitor employee Internet activity when offenses first occurred in the workplace.
Within two months, Goldberg hired a half-dozen more software developers and tapped a CIO with 15 years of experience to take on the role of chief operating officer.
Trouble lurked beneath the surface, however. Two of the company's software developers approached ITTI's new COO and demanded that the company "pay them a lot of money or they will resign immediately and not provide any assistance to the development team.”
Faced with the equivalent of a cyberhijacking, he refused to budge, and the developers were dismissed.
The first denial-of-service attack hit the next morning, a Thursday, and crashed the company's application server…The situation soon became critical. "If the attacks continued to go on, we would go out of business," Goldberg says. He called in a security consulting firm and the Secret Service.
The last attack, which occurred Monday morning, hit as federal authorities were installing monitoring equipment on ITTI's networks. Authorities traced the attacker to a computer at Queens College in Flushing, N.Y., where one of the former employees was a student. Witnesses placed the individual at the specific computer at the precise time of the attack. Within an hour, the Secret Service officials had their man. No evidence or charges were brought against the other former employee.
Use SurveilStar to monitor your employee's network activities
SurveilStar is the trustworthy PC/Internet monitoring software that helps to secure your business and improve productivity and efficiency. SurveilStar is feature-rich, easy and intuitive.
What’s important, SurveilStar puts you in control. Whatever you can monitor, you can control it. You can control certain computer’s access to websites, filter outgoing files via IM, block email attachment, disable removable device drive, cancel unauthorized file sharing, prevent changing system configurations, and many more. You can even lock the target computer if potential sabotage is out there.
Stealth mode, all-around records and reports, real-time multi-screen snapshot monitoring, dynamic PC/Internet control strategies, all these combine to build a complete solution for protecting your intellectual properties and business secrets, reducing slackers, prevent Internet and email abuse and related potential legal liability, and improve productivity.
Statistics, event logs, policies, instant message contents, emails and asset management all can be exported and saved as HTML/Excel/Text (CSV) files.